Contents
Overview
* Kerberos provides authentication and crypto over the network.
Benefits of Kerberos
* Faster connections:
– server does not need to contact domain controller (DC) in order to authenticate clients.
– clients carries with them session tickets for target servers.
* Mutual authentication:
– two way authentication between server and client
* Delegated authentication:
– proxy mechanism that allows a Windows service to impersonate its client when connecting to other services
* Simplified trust management
– trusts are mutual and transitive
* Interop with non Windows 2000 network resources via on Kerveros 5
Three Heads of Kerberos
* Key Distribution Center (KDC)
* User Client
* Server resource
Key Distribution Center: KDC
* KDC runs on a physically secure server.
* KDC maintains a database with account info for all security principals in its realm aka domain.
* KDC stores a cryptographic key known only to the security principal and the KDC.
– aka long-term key which is usually derived from user password, e.g. hash value.
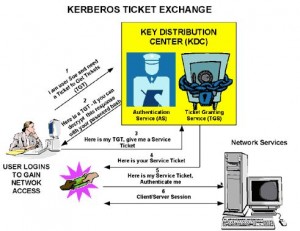
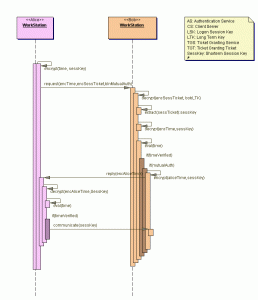
Key Exchanges
AS Exchange
* AS: Authentication Service
TGS Exchange
* TGS: Ticket Granting Service
CS Exchange
* CS: Client Server
Kerberos in Active Directory
* Integral part of AD 2000 (NTLM only before it)
* Uses Kerberos verion 5
* KDC is part of domain controller and servers as:
– the Authentication Service (AS)
– the Ticket Granting Service (TGS)
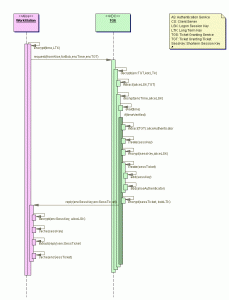
TGT
* TGT is
– valid for the local domain
– cached on local machine in volatile memory space
– used to request sessions with services throughout the network
* TGT contains two sections:
– a TGT ticket encrypted with a key that only KDC(TGS) can decrypt
– a session key encrypted with user’s password hash to handle future communications
* TGT includes:
– TTL which defaults to 8 hrs
– authorization data
– session key
References
* Windows 2000 Kerberos Authentication
* Kerberos: The Network Authentication Protocol
* http://www.mcmcse.com/microsoft/guides/kerberos.shtml
* Kerberos Explained