Contents
Sign up for a Duo Account
* Sign up for a Duo account here
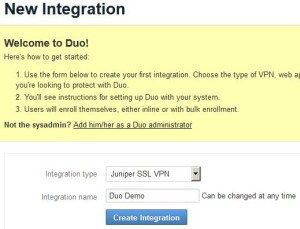
Create a new Juniper SSL VPN Integration
* Login Duo Admin Panel
* Select Integration > New Integration to bring up New Integration page
* Select:
– Integration type: Juniper SSL VPN
– Integration name: Duo Demo
* Click Create Integration button
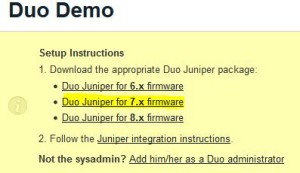
* Download Duo Juniper for 7.x firmware, e.g. Duo-Juniper-7.x-v7-2932-6069-68.zip
Configure Juniper SSL VPN
* Login Juniper admin console
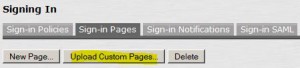
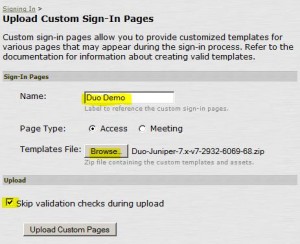
Modify Sign-In Page
* Select Authentication > Signing In > Sign-In Pages
* Click Upload Custom Pages…
* Enter:
– Name: Duo Demo
– Page Type: Access
– Templates File: browse to Duo-Juniper-7.x-v7-2932-6069-68.zip
– Skip validation checks during upload: checked
* Click Update Custom Pages
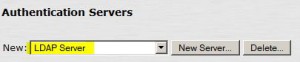
Add Duo LDAP Auth Server
* Select Authentication > Auth. Servers
* Select New: LDAP Server
* Click New Server…
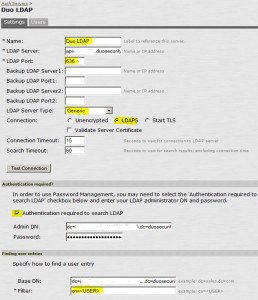
* Enter:
– Name: Duo LDAP
– LDAP Server: replace_with_APIHostname
– LDAP Port: 636
– LDAP Server Type: Generic
– Connection: LDAPS
– Authentication required to search LDAP: checked
– Admin DN: dc=replace_with_integration_key,dc=duosecurity,dc=com
– Password: secret_key
– Base DN: dc=replace_with_integration_key,dc=duosecurity,dc=com
– Filter: cn=<USER>
* Click Save and ignore warning message:
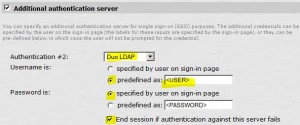
Configure Secondary Auth Server for a User Realm
* Select Users > User Realms > Select Realm
* Check Additional authentication server checkbox
* Select or enter:
– Authentication #2: Duo LDAP
– Username is: predefined as <USER>
– Password is: specified by user on sing-in page
– End session if authentication against this server fails: checked
* Click Save Changes
* Select Authentication Policy > Password
* On Options for additional authentication server panel, select:
Allow all users (passwords of any length)
* Click Save Changes
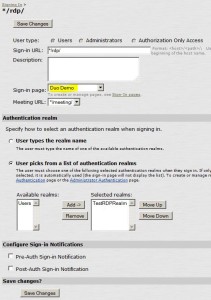
Configure Sign-In Policy for Secondary Auth
* Select Authentication > Signing In > Sign-in Policies
* Select sign-in policy that you want to add duo security, e.g. */rdp/
* Select
– Duo Demo from the Sign-in page list
– Selected realms: realm_configured_previously
* Click Save Changes
Test
Create Duo User
* Login Duo Admin site
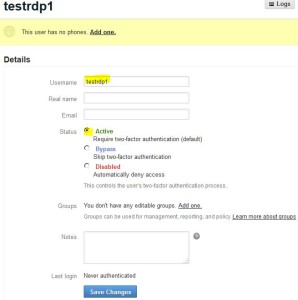
* Select Users > +New User
* Add a new user with username matching your Juniper user, e.g testrdp1
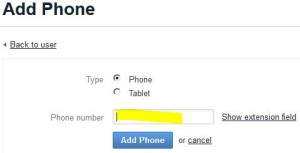
* Add a phone for the newly created user
Test Juniper VPN
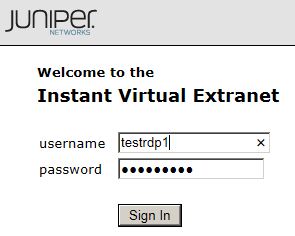
* Login Juniper VPN as usual
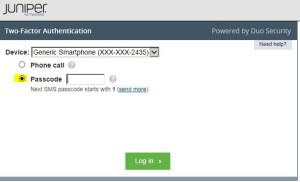
* Click SMS to send text code
* Enter received text code into Passcode field
* Click Log in > button
* You should be logged in

The SPE is meant for service pdroirevs, as is reflected in its subscription licensing model, isn’t it? Most healthcare customers, and certainly the ones that this white paper is aimed at, are individual health care pdroirevs hospitals and such. Who’d be running vGW on their own VMWare infrastructure.I think the idea of having the option of a virtual SSL VPN gateway for enterprise customers is a great one. Just that, right now, that doesn’t seem available.Am I missing something?VA:F [1.9.22_1171]please wait…