Contents
Setup OpenDJ LDAP Server
* See this post
Start OpenDJ
* Start OpenDJ: OpenDJ_Home/bin/start-ds
LDAP to OpenIDM
* Go to OpenIDM home directory:
$ ls
audit cli.sh curl logs security startup.sh
bin conf db samples shutdown.sh workflow
bundle connectors felix-cache script startup.bat* Shutdown OpenIDM if running.
* Copy configuration files from sampes/sample2 directory:
cp -r samples/sample2/conf .
* Startup OpenIDM
./startup.sh* Retrieve all users before reconciliation:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" http://localhost:8080/openidm/managed/user/?_query-id=query-all-ids {"query-time-ms":0,"result":[],"conversion-time-ms":0}
* Initiate reconciliation:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" \ --request POST "http://localhost:8080/openidm/sync?_action=recon&mapping=systemLdapAccounts_managedUser" {"reconId":"edcec6d0-bf75-42fe-9aef-9f40d6d1e7fc"}
* Retrieve all users after reconciliation:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" http://localhost:8080/openidm/managed/user/?_query-id=query-all-ids {"query-time-ms":1,"result":[{"_id":"9fcd9018-37d1-4a48-9ee5-b9c14fd4cc2d","_rev":"0"}],"conversion-time-ms":0}
OpenIDM <- to/from -> LDAP
Copy Scripts
* Go to OpenIDM home directory.
* Shutdown OpenIDM if running.
* Copy sample scripts:
cp -r samples/sample2b/conf . cp -r samples/sample2b/script . # Alernatively: cp samples/sample2b/script/ldapBackCorrelationQuery.js script/ manually append "managedUser_systemLdapAccounts" section from samples/sample2b/conf/sync.json to conf/sync.json
* conf/sync.json specifies mappings:
– ldap – to -> OpenIDM:
{ "mappings" : [ { "name" : "systemLdapAccounts_managedUser", "source" : "system/ldap/account", "target" : "managed/user", "properties" : [ { "source" : "cn", "target" : "displayName" }, ... }
– OpendIDM – to -> ldap:
{ "name" : "managedUser_systemLdapAccounts", "source" : "managed/user", "target" : "system/ldap/account", "links" : "systemLdapAccounts_managedUser", "correlationQuery" : { "type" : "text/javascript", "file" : "script/ldapBackCorrelationQuery.js" }, "properties" : [ { "source" : "givenName", "target" : "givenName" }, ...
Synchronize
* Start OpenIDM.
* Retrieve all users before synchronization:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" http://localhost:8080/openidm/managed/user/?_query-id=query-all-ids
* Synchronize:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" \ --request POST \ "http://localhost:8080/openidm/sync?_action=recon&mapping=systemLdapAccounts_managedUser" {"reconId":"e0e7fcd0-c8f1-4960-8fb2-d34b9ba2c8bd"}
* Retrieve all users after synchronization:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" http://localhost:8080/openidm/managed/user/?_query-id=query-all-ids {"query-time-ms":1,"result":[{"_id":"9fcd9018-37d1-4a48-9ee5-b9c14fd4cc2d","_rev":"0"}],"conversion-time-ms":0}
* Manually add a user to OpenIDM:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" \ --request PUT \ --data "{\"email\":\"fdoe@example.com\",\"familyName\":\"Doe\",\"userName\":\"fdoe\", \ \"givenName\":\"Felicitas\",\"displayName\":\"Felicitas Doe\"}" "http://localhost:8080/openidm/managed/user/repoUser1" {"_id":"repoUser1","_rev":"0"}
* Synchronize again:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" \ --request POST "http://localhost:8080/openidm/sync?_action=recon&mapping=systemLdapAccounts_managedUser" {"reconId":"6b5d31ff-199f-48c6-b00a-d705ab943759"}
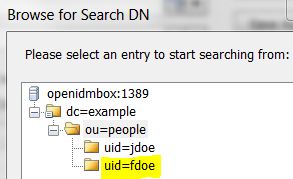
* Check LDAP for new user synched from OpenIDM
LDAP <- to/from -> LDAP
[jli@openidmbox Desktop]$ cd /opt/openidm/openidm/ [jli@openidmbox openidm]$ ls audit cli.sh curl --header samples shutdown.sh workflow bin conf db logs script startup.bat bundle connectors felix-cache --request security startup.sh [jli@openidmbox openidm]$ cp -r samples/sample6/conf .
CSV to OpenIDM
* Copy $OPENIDM_HOME/samples/sample4/conf/provisioner.openicf-csv.json to $OPENIDM_HOME/conf
cd $OPENIDM_HOME/ cp samples/sample4/conf/provisioner.openicf-csv.json conf
$ pwd /opt/openidm/builtFromSrc/openidm $ cp samples/sample4/conf/provisioner.openicf-csv.json conf $ cat conf/provisioner.openicf-csv.json { "name" : "HR", "connectorRef" : { "connectorHostRef" : "#LOCAL", "connectorName" : "org.forgerock.openicf.csvfile.CSVFileConnector", "bundleName" : "org.forgerock.openicf.connectors.file.openicf-csvfile-connector", "bundleVersion" : "1.1.0.0" }, "poolConfigOption" : { "maxObjects" : 10, "maxIdle" : 10, "maxWait" : 150000, "minEvictableIdleTimeMillis" : 120000, "minIdle" : 1 }, "operationTimeout" : { "CREATE" : -1, "VALIDATE" : -1, "TEST" : -1, "SCRIPT_ON_CONNECTOR" : -1, "SCHEMA" : -1, "DELETE" : -1, "UPDATE" : -1, "SYNC" : -1, "AUTHENTICATE" : -1, "GET" : -1, "SCRIPT_ON_RESOURCE" : -1, "SEARCH" : -1 }, "configurationProperties" : { "filePath" : "data/hr.csv", "uniqueAttribute" : "uid", "nameAttribute" : "uid", "passwordAttribute" : "password" }, "objectTypes" : { "account" : { "$schema" : "http://json-schema.org/draft-03/schema", "id" : "__ACCOUNT__", "type" : "object", "nativeType" : "__ACCOUNT__", "properties" : { "employeeNumber" : { "type" : "string", "nativeName" : "employeeNumber", "nativeType" : "string" }, "mail" : { "type" : "string", "nativeName" : "email", "nativeType" : "string" }, "uid" : { "type" : "string", "required" : true, "nativeName" : "__NAME__", "nativeType" : "string" }, "password" : { "type" : "string", "nativeName" : "__PASSWORD__", "nativeType" : "JAVA_TYPE_GUARDEDSTRING", "flags" : [ ] }, "lastName" : { "type" : "string", "required" : true, "nativeName" : "lastName", "nativeType" : "string" }, "givenName" : { "type" : "string", "nativeName" : "firstName", "nativeType" : "string" } } } }, "operationOptions" : { } }
* Add systemHrAccounts_managedUser mapping to conf/sync.json
{ "name" : "systemHrAccounts_managedUser", "source" : "system/HR/account", "target" : "managed/user", "properties" : [ { "source" : "employeeNumber", "target" : "employeeNumber" }, { "source" : "mail", "target" : "email" }, { "source" : "uid", "target" : "userName" }, { "source" : "uid", "target" : "_id" }, { "source" : "lastName", "target" : "familyName" }, { "source" : "givenName", "target" : "givenName" }, { "source" : "password", "target" : "password" } ], "policies" : [ { "situation" : "CONFIRMED", "action" : "UPDATE" }, { "situation" : "FOUND", "action" : "UPDATE" }, { "situation" : "ABSENT", "action" : "CREATE" }, { "situation" : "AMBIGUOUS", "action" : "EXCEPTION" }, { "situation" : "MISSING", "action" : "UNLINK" }, { "situation" : "SOURCE_MISSING", "action" : "IGNORE" }, { "situation" : "UNQUALIFIED", "action" : "IGNORE" }, { "situation" : "UNASSIGNED", "action" : "IGNORE" } ] }
* Copy $OPENIDM_HOME/samples/sample4/data/hr.csv to $OPENIDM_HOME/data directory
cd $OPENIDM_HOME mkdir data cp samples/sample4/data/hr.csv data
* Restart OpenIDM
* Query all ids:
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" http://localhost:8080/openidm/managed/user/?_query-id=query-all-ids {"query-time-ms":1,"result":[{"_id":"3A066F86-D822-488F-9A21-FEA8E1A03C43","_rev":"0"}],"conversion-time-ms":0}
* Run reconciliation
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" \ --request POST "http://localhost:8080/openidm/sync?_action=recon&mapping=systemHrAccounts_managedUser" {"reconId":"926af8c3-3751-492e-b2d6-406a9fe735db"}
* Query all ids again and should get a new id: “_id”:”DDOE”
curl \ --header "X-OpenIDM-Username: openidm-admin" \ --header "X-OpenIDM-Password: openidm-admin" http://localhost:8080/openidm/managed/user/?_query-id=query-all-ids {"query-time-ms":7,"result":[{"_id":"3A066F86-D822-488F-9A21-FEA8E1A03C43","_rev":"0"},{"_id":"DDOE","_rev":"0"},{"_id":"VDART","_rev":"0"}],"conversion-time-ms":0}
References
* OpenIDM 2.1.0 Installation Guide: Chapter 3. More OpenIDM Samples