Contents
Environment
* JBoss 5.1.0.GA or JBoss 4.2.2.GA
* Centos version:
[root@jboss01 ~]# cat /etc/redhat-release CentOS release 5.7 (Final) [root@jboss01 ~]# uname -m x86_64
* Java version:
java version "1.6.0_24" OpenJDK Runtime Environment (IcedTea6 1.11.11.90) (rhel-1.41.1.11.11.90.el5_9-x86_64) OpenJDK 64-Bit Server VM (build 20.0-b12, mixed mode)
Prepare
* Install JBoss 5.1 AS. See this post for details.
Download PicketLink
* Download version v2.1.8.Final from here
– Core jar: picketlink-core-2.1.8.Final.jar
– Binding jar for AS 5.x: picketlink-jbas5-2.1.8.Final.jar
* For JBOss 4.2.2.GA, also download jboss-security-spi-3.0.0.Final.jar from here
Generate JKS Keystore
Generate keystore using Java keytool
* Generate private key:
keytool -genkey -alias jboss01 -keyalg RSA -sigalg SHA1withRSA -keysize 2048 -keystore jboss01.jks -storepass Welcome1 -keypass Welcome1 -dname "CN=jboss01.mytest.local, OU=Lab, O=My Test, L=Reston, S=Virginia, C=US" -validity 360
* Generate CSR:
keytool -certreq -alias jboss01 -sigalg SHA1withRSA -file jboss01.csr -keystore jboss01.jks -storepass Welcome1
* Send CSR to CA for signing.
* Import signed certificate:
keytool -import -v -keystore jboss01.jks -alias jboss01 -storepass Welcome1 -file jboss01.p7b
Generate keystore using Portecle
* Download Portecle from http://sourceforge.net/projects/portecle/
* Start Portecle:
java -jar portecle.jar
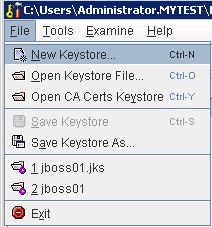
Generate New Key Store
* Select File > New Keystore…
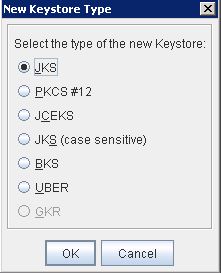
* Select JKS as store type:
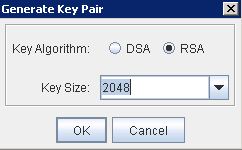
* Select Tools > Generate Key Pair… and select:
– Key Algorithm: RSA
– Key Size: 2048
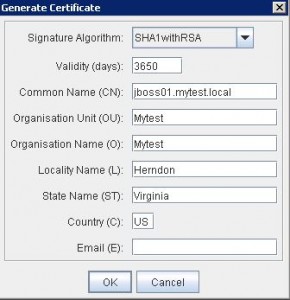
* Enter CN for the new key:
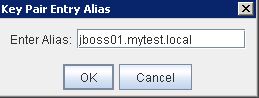
* Enter alias for the new key:
* Keystore pass (e.g. Welcome1):
* Keystore generated:
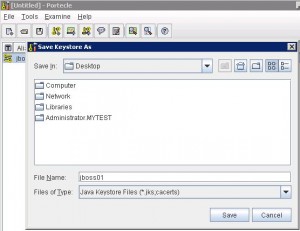
* Save keystore file jboss01.jks:
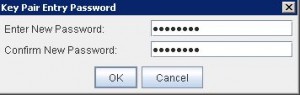
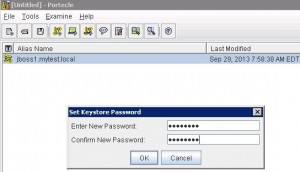
* Set Keystore file password (e.g. Welcome1):
Generate CSR
* Right click keystore entry and select Generate Certification Request
– File Name: jboss01_mytest_local.csr
* Submit to CA for signing
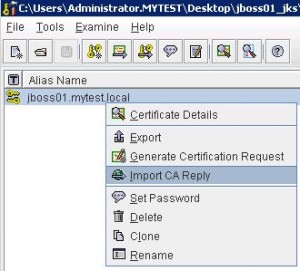
Import CA Reply
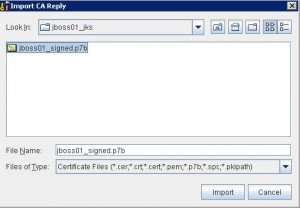
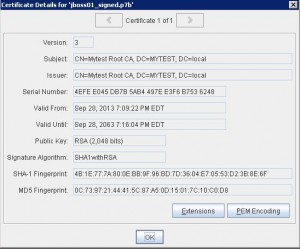
* Import CA reply:
Configure Keystore on JBoss AS
* Copy jboss01.jks to $JBOSS_HOME/server/default/conf
* Config JBoss AS to use the keystore
vi $JBOSS_HOME/server/default/deploy/jbossweb.sar/server.xml
<Connector protocol="HTTP/1.1" SSLEnabled="true” port="8443"
address="${jboss.bind.address}"
scheme="https" secure="true" clientAuth="false"
keystoreFile="${jboss.server.home.dir}/conf/jboss01.jks" keystorePass="Welcome1"
sslProtocol = "TLS" />* Restart JBoss
* Open port 8443
-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 8443 -j ACCEPT service iptables restart
* Check https connection:
Setup NTP
* All servers should setup NTP clients.
Export ADFS Token Signing Cert
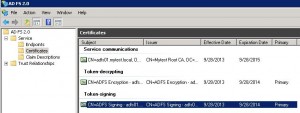
* Go to: AD FS 2.0 console, open AD FS 2.0 > Service > Certificates
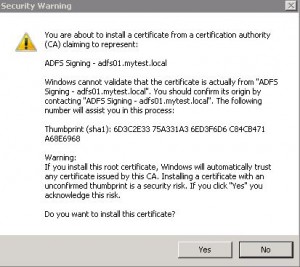
* Select: Token-signing certificate > View Certificate
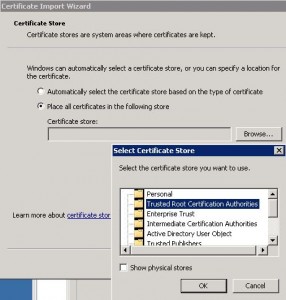
* Install as Trusted Root Certificate if prompted
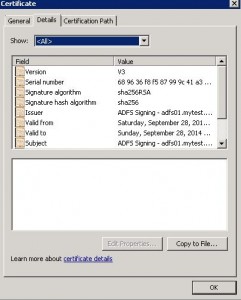
* Select: Token-signing certificate > View Certificate > Details
* Click Copy to File…
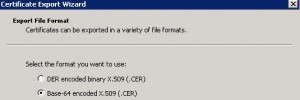
* Select Base-64 encoded X.509 (.CER)
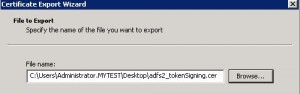
* File name: adfs2_tokenSigning.cer
Create AD FS Trust Store
* Generate a new key store
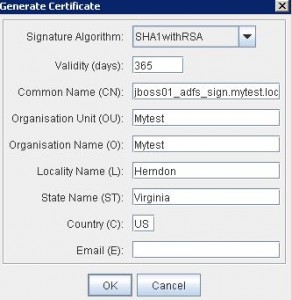
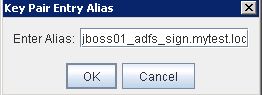
* Generate a new key pair with CN: jboss01_adfs_sign.mytest.local
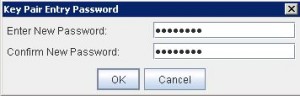
* Save as file name: jboss01_adfs_sign.jks with password, e.g. Welcome1
* Import ADFS token signing certificate, i.e. adfs2_tokenSigning.cer created previously.
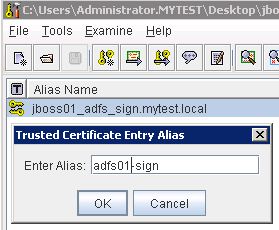
– Select Tools > Import Trusted Certificate…
– Enter Alias: adfs01-sign
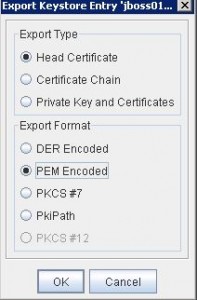
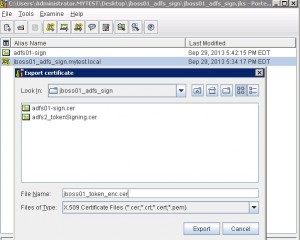
* Export keystore certificate. The certificate is used as encryption certificate by ADFS2:
– Right click keystore, select Export then select PEM Encoded:
* Enter file name: jboss01_token_enc.cer
Install PicketLink Library Files
Copy Jar Files to JBoss common lib Directory
* Copy following files to $JBOSS_HOME/common/lib directory
– picketlink-core-2.1.8.Final.jar
– picketlink-jbas5-2.1.8.Final.jar
* For JBoss 4.2.2, copy instead to $JBOSS_HOME/server/default/lib directory:
– picketlink-core-2.1.8.Final.jar
– picketlink-jbas5-2.1.8.Final.jar
– jboss-security-spi-3.0.0.Final.jar
* Setup file permissions:
chmod 644 picketlink*jar
Authorize PicketLink jar Files
* For EAP 5.1, edit $JBOSS_HOME/bin/security_cc.policy and grant permission to PicketLink jar files:
// Picketlink libraries grant codeBase "file:${jboss.home.dir}/common/lib/picketlink-core-2.1.7.jar" { permission java.security.AllPermission; }; grant codeBase "file:${jboss.home.dir}/common/lib/picketlink-jbas5-2.1.7.jar" { permission java.security.AllPermission; };
Configure PicketLink Authenticator
* Add to $JBOSS_HOME/server/default/deployers/jbossweb.deployer/META-INF/war-deployers-jboss-beans.xml after the BASIC entry:
<entry> <key>SAML_FEDERATION</key> <value>org.picketlink.identity.federation.bindings.tomcat.sp.ServiceProviderAuthenticator</value> </entry>
* For JBoss 4.2.2, add instead to $JBOSS_HOME/server/default/deploy/jboss-web.deployer/META-INF/jboss-service.xml:
<java:property> <java:key>SAML_FEDERATION</java:key> <java:value>org.picketlink.identity.federation.bindings.tomcat.sp.ServiceProviderAuthenticator</java:value> </java:property>
Configure login.module
* Setup a PicketLink SAML2 Login Module by adding to $JBOSS_HOME/server/default/conf/login-config.xml:
<application-policy name="saml-federation-hw"> <authentication> <login-module code="org.picketlink.identity.federation.bindings.jboss.auth.SAML2LoginModule" flag="required" /> </authentication> </application-policy>
Configure PicketLink Properties
* Create a directory named /home/jboss/picketlink to place PicketLink property file.
* Create a file named picketlink.properties in the newly created directory with the following content:
# Identity Provider configuration picketlink.idp.domain=mytest.local picketlink.idp.public.fqdn=adfs01.mytest.local picketlink.idp.public.url=https://adfs01.mytest.local/adfs/ls/ # Service Provider configuration picketlink.sp.public.fqdn=jboss01.mytest.local picketlink.sp.public.port=8443 # Trust Store configuration picketlink.truststore.url=file:///home/jboss/picketlink/jboss01_adfs_sign.jks picketlink.truststore.password=Welcome1 picketlink.truststore.idp.alias=adfs01-sign
* Setup file permissions:
chmod 400 picketlink.properties
* Expose picketlink.properties file by adding to $JBOSS_HOME/server/default/deploy/properties-service.xml file’s SystemPropertiesService mbean:
<attribute name="URLList"> /home/jboss/picketlink/picketlink.properties </attribute>
Copy ADFS Signing Keystore
* Copy jbooss01_adfs_sign.jks to /home/jboss/picketlink directory
Configure WAR (hw.war) Deployment
Create a Test Web App
* Create a temp directory to host all files
* Create a jsp file named default.jsp:
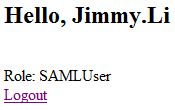
<html> <head> <title>JSP Test</title> <% String userId = null; if (request.getUserPrincipal() != null){ userId = request.getUserPrincipal().getName(); }else{ userId = request.getRemoteUser(); } if (userId == null){ userId = "World"; } String message = "Hello, " + userId; %> </head> <body> <h2><%= message%></h2> <% if (request.isUserInRole("SAMLUser")){ %> <br/> Role: SAMLUser <%}%> <br/> <a href="https://adfs01.mytest.local/adfs/ls/?wa=wsignout1.0">Logout</a> </body> </html>
* Create a new directory named WEB-INF
* Create a new file named web.xml:
<web-app> <display-name>Hello World</display-name> </web-app>
* Jar all files into war file:
"%JAVA_HOME%\jar" -cvf hw.war *
* Copy hw.war file to $JBOSS_HOME/server/default/deploy directory
$JAVA_HOME/bin/jar -cvf hw.war * # Win "%JAVA_HOME%/bin/jar" -cvf hw.war *
* Check that page is displayed properly.
Configure Application Security Constraints
* Add to web.xml:
<security-constraint> <web-resource-collection> <web-resource-name>All Pages</web-resource-name> <url-pattern>/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>SAMLUser</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> <security-role> <role-name>SAMLUser</role-name> </security-role>
* Add to web.xml a new constraint to act as SAML Assertion Consumer Service.
– url-pattern is not significant and does not map to any actual resource:
<security-constraint> <web-resource-collection> <web-resource-name>SAML HW</web-resource-name> <url-pattern>/saml-hw</url-pattern> </web-resource-collection> <auth-constraint> <role-name>*</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint>
Configure login module
* Add to web.xml
<login-config> <auth-method>SAML_FEDERATION</auth-method> <realm-name>SAML Federation</realm-name> </login-config>
Final web.xml File
<web-app> <display-name>Hello World</display-name> <security-constraint> <web-resource-collection> <web-resource-name>All Pages</web-resource-name> <url-pattern>/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>SAMLUser</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>SAML HW</web-resource-name> <url-pattern>/saml-hw</url-pattern> </web-resource-collection> <auth-constraint> <role-name>*</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> <login-config> <auth-method>SAML_FEDERATION</auth-method> <realm-name>SAML Federation</realm-name> </login-config> <security-role> <role-name>SAMLUser</role-name> </security-role> </web-app>
Update Security Domain
* Edit WEB-INF/jboss-web.xml to use PicketLink login module defined previously:
<?xml version='1.0' encoding='UTF-8' ?> <!DOCTYPE jboss-web PUBLIC "-//JBoss//DTD Web Application 2.3V2//EN" "http://www.jboss.org/j2ee/dtd/jboss-web_3_2.dtd"> <jboss-web> <security-domain>java:/jaas/saml-federation-hw</security-domain> </jboss-web>
Create WEB-INF/context.xml File
<?xml version="1.0" encoding="UTF-8"?> <Context> <Valve className="org.picketlink.identity.federation.bindings.tomcat.sp.ServiceProviderAuthenticator" /> </Context>
Create WEB-INF/picketlink.xml File
<PicketLink xmlns="urn:picketlink:identity-federation:config:2.1"> <PicketLinkSP xmlns="urn:picketlink:identity-federation:config:2.1" CanonicalizationMethod="http://www.w3.org/2001/10/xml-exc-c14n#" BindingType="POST" IDPUsesPostBindings="true" SupportsSignatures="true"> <IdentityURL>${picketlink.idp.public.url}</IdentityURL> <ServiceURL>https://${picketlink.sp.public.fqdn}:${picketlink.sp.public.port}/hw/saml-hw</ServiceURL> <Trust> <Domains>${picketlink.idp.domain}</Domains> </Trust> <KeyProvider ClassName="org.picketlink.identity.federation.core.impl.KeyStoreKeyManager"> <Auth Key="KeyStoreURL" Value="${picketlink.truststore.url}"/> <Auth Key="KeyStorePass" Value="${picketlink.truststore.password}"/> <Auth Key="SigningKeyAlias" Value="NOTUSED"/> <Auth Key="SigningKeyPass" Value="NOTUSED"/> <ValidatingAlias Key="${picketlink.idp.public.fqdn}" Value="${picketlink.truststore.idp.alias}"/> </KeyProvider> </PicketLinkSP> <Handlers xmlns="urn:picketlink:identity-federation:handler:config:2.1"> <Handler class="org.picketlink.identity.federation.web.handlers.saml2.SAML2IssuerTrustHandler" /> <Handler class="org.picketlink.identity.federation.web.handlers.saml2.SAML2SignatureValidationHandler" /> <Handler class="org.picketlink.identity.federation.web.handlers.saml2.SAML2LogOutHandler" /> <Handler class="org.picketlink.identity.federation.web.handlers.saml2.SAML2AuthenticationHandler"> <Option Key="ROLE_KEY" Value="http://schemas.microsoft.com/ws/2008/06/identity/claims/role"/> </Handler> <Handler class="org.picketlink.identity.federation.web.handlers.saml2.SAML2AttributeHandler"/> </Handlers> </PicketLink>
* Jar all files and deploy to JBoss as described previously.
Create ADFS relying party named jboss01-PicketLink
* Login ADFS server, e.g. adfs01, as domain administrator.
* Open AD FS 2.0 console
* Go to AD FS 2.0 > Trust Relationships > Replying Party Trusts
* Right click and select Add Relying Party Trust…
* Click Start on Welcome page:
* Select Enter data about the relying party manually
* Enter
– Display name: jboss01.mytest.local:8443/hw
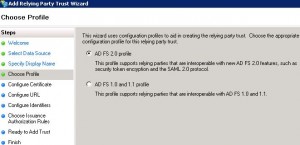
* Select AD FS 2.0 profile
* (Skip for now)Configure Certificate by browsing to jboss01_token_enc.cer
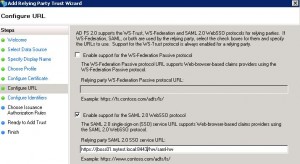
* Select Enable support for the SAML 2.0 WebSSO protocol and enter:
– Replying party SAML 2.0 SSO service URL: https://jboss01.mytest.local:8443/hw/saml-hw
and click Add button:
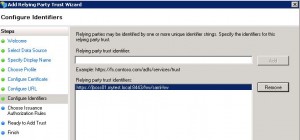
* On Configure Identifiers screen, enter
– Relying party trust identifier: https://jboss01.mytest.local:8443/hw/saml-hw
* On Choose Issuance Authorization Rules, select:
– Permit all users to access this relying party
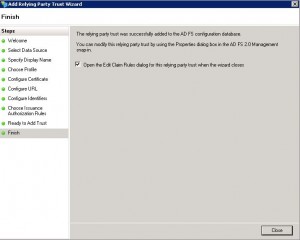
* On Ready to Add Trust screen, click Next>
* On Finish screen, select Open the Edit Claim Rules and click Close
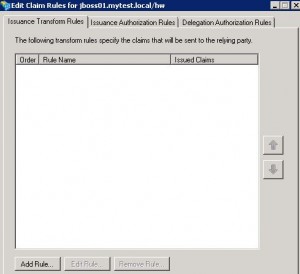
* Edit Claim Rules for jboss01.mytest.local/hw opens
Add Claim Rule for SAM-Account-Name
* Select Issuance Transform Rules tab
* Click Add Rule…
* Select Send LDAP Attributes as Claims
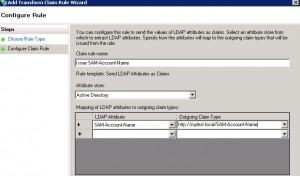
* Enter:
– Claim rule name: Issue SAM-Account-Name
– Attribute store: Active Directory
– Mapping of LDAP attributes to outgoing claim types:
LDAP Attribute: SAM-Account-Name
Outgoing Claim Type: http://mytest.local/SAM-Account-Name
Add Claim Rule for Name ID
* Select Issuance Transform Rules tab
* Click Add Rule
* Select Transform an Incoming Claim and click Next:
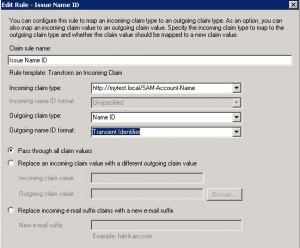
* Configure claim rule:
– Claim rule name: Issue Name ID
– Incoming claim type: http://mytest.local/SAM-Account-Name
– Outgoing claim type: Name ID
– Outgoing name ID format: Transient Identifier
– Select: Pass through all claim values
* Click Finish
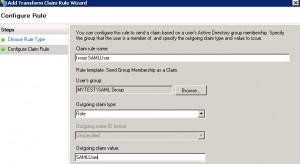
Add Claim Rule for Role
* Still on Issuance Transform Rules tab
* Click Add Rule…
* Select Send Group Membership as a Claim:
* Configure claim rule:
– Claim rule name: Issue SAMLUser
– User’s group: MYTEST\SAML Group (note this is an existing group in MYTEST domain)
– Outgoing claim type: Role
– Outgoing claim value: SAMLUser (note that this need to match the role as defined in web application’s web.xml file)
* Click Finish
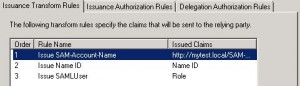
* Click OK to add the newly configured Relying Party. Three rules are shown:
Add SAML Logout Endpoint
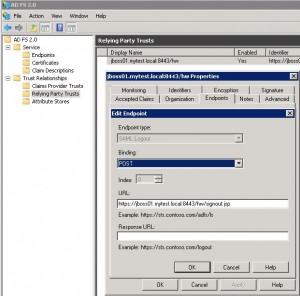
* From AD FS 2.0 console, go to AD FS 2.0 > Trust Relationships > Relying Party Trusts
* Right click jboss01.mytest.local:8443/hw relying party and select Properties
* Select Endpoints tab and click Add
* On Add an Endpoint screen, enter:
– Endpoint type: SAML Logout
– Binding = POST
– URL: https://jboss01.mytest.local:8443/hw/signout.jsp # This is the application logout page and should not be protected.
– Response URL: <Can be left empty>
* Click OK twice.
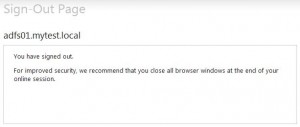
* Add logout URL on web site logout link: https://adfs01.mytest.local/adfs/ls/?wa=wsignout1.0
Test
* Import MytestRootCA.cer as Trusted Root Certificate Authorities
* Point browser to https://jboss01.mytest.local:8443/hw/default.jsp
* Enter username and password when prompted.
– Note that you will not be prompted for username and password if you logged into a domain computer.
* The page is displayed:
* Click the Logout link, ADFS logout page is displayed:
IDP Initiated Sign on URL
* https://adfs01.mytest.local/adfs/ls/IdpInitiatedSignOn.aspx
SAML Tracer
* Install SAML Tracer Addon for Firefox
* Open SAML Tracer console from Tools > SAML tracer
* Example:
<samlp:Response ID="_4d71a2dd-b0b9-4e19-a0c1-a1718adb6f1f" Version="2.0" IssueInstant="2013-10-01T23:41:10.278Z" Destination="https://jboss01.mytest.local:8443/hw/saml-hw" Consent="urn:oasis:names:tc:SAML:2.0:consent:unspecified" InResponseTo="ID_8af19346-3479-4eac-9076-2b37f6d2c31f" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" > <Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">http://adfs01.mytest.local/adfs/services/trust</Issuer> <samlp:Status> <samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" /> </samlp:Status> <Assertion ID="_610520ab-d49d-49cc-95fb-c82bcf555af8" IssueInstant="2013-10-01T23:41:10.277Z" Version="2.0" xmlns="urn:oasis:names:tc:SAML:2.0:assertion" > <Issuer>http://adfs01.mytest.local/adfs/services/trust</Issuer> <ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> <ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" /> <ds:Reference URI="#_610520ab-d49d-49cc-95fb-c82bcf555af8"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" /> <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" /> <ds:DigestValue>M2oIWu3zrkQxt8t/ARsSkape8m3nUNb8u0F9OiSVqy0=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <ds:SignatureValue>aLInCoeyPfAA5Yt+ppCCr0vR4c2/g2gFf8WtosdzNQgeewwhTNGQKF+DIK3OpkhiIlHZ8v58S+QO5DH5KeJ8NjuhIgujVNIbDev6+6eneIuXVx2HUZZwH8zhdj/MT8Pir0BQq8/BtC8wHzDWmyxmRH0fJ8rZ479ODJzqABWxdkPhkDoiIRiCrjCyZekGnwVlfi9tCVCs1Xs50txkOTpbQLODQf4PyLWzhZPghcNkrR1M8r9e+J3/mtGAQHKeHI/Ih/WRic+nDHpPKi4PBAUZFcwQCkqku2SrQXecQJ3eLfZA6ujYJHSWHzoMuTFFRLY0Hnuwc3sMmZLbxLx7asrJVQ==</ds:SignatureValue> <KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#"> <ds:X509Data> <ds:X509Certificate>MIIC4jCCAcqgAwIBAgIQaJY2+PWHmZxBo3mRmD1JCzANBgkqhkiG9w0BAQsFADAtMSswKQYDVQQDEyJBREZTIFNpZ25pbmcgLSBhZGZzMDEubXl0ZXN0LmxvY2FsMB4XDTEzMDkyODIzNDQxMloXDTE0MDkyODIzNDQxMlowLTErMCkGA1UEAxMiQURGUyBTaWduaW5nIC0gYWRmczAxLm15dGVzdC5sb2NhbDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKuuRT6vQ+XuzEq69yGlIsyttykycdOOf85VEZ7OKnFMN4H6zpp+OrjhFI4GBhjBIrX+BcgGauan18DPOs9mVl7AYS1iLtZay6cJ/Nz8O5m66TPiB+k07pu6SdE23WOzxVotf6jwY8b+9DtDcy6ck3yCUBIHIpJ8dgn7we4/yPFWY5ARHBJ0s5rsP2sDO3SQNz2ZZ9bKZxePnoScFDoM5mK0BOBqQuxGKi/YtF+JdfYG5V1OuHlx3Oe0Ybyx9xSKdP1NAjbvWMrN3SptbBLixOguXTEkfAzYB6UZKi183yElV/VogMGixRVu38a4R3w4yyXlYcshH7hwP07L4+hodTUCAwEAATANBgkqhkiG9w0BAQsFAAOCAQEAolGuUbbv+d0E3OvjCDunOJVznYSAnca3HBToWItwHbM0MvXaft/Kq+CV+vrPuaVM+n/RJndqzMY5PUDAInOmVM72BGyKhgl8C899PfClsLcKBLQJciTRHRekLLv66wp2lFlF3VVaRc+U+6tQFW62l2ITAdyPp34NEk5TQVBh9A5L03WdMkiWJzXRGob8lTuFmBc15FUFE+noqT5Q+EP8LU5t54/KaEr+9vLNqR6pCJePemHOZLXcxozSmMUEuCfi551g875TBT88feSVWBuW6FqfrTFPD9i4Lub5TjDPZ0S9zHuePzFjJ6KvLadtDva+r4aNV+NUR5UT5loJcVnqVQ==</ds:X509Certificate> </ds:X509Data> </KeyInfo> </ds:Signature> <Subject> <NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient">Jimmy.Li</NameID> <SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <SubjectConfirmationData InResponseTo="ID_8af19346-3479-4eac-9076-2b37f6d2c31f" NotOnOrAfter="2013-10-01T23:46:10.278Z" Recipient="https://jboss01.mytest.local:8443/hw/saml-hw" /> </SubjectConfirmation> </Subject> <Conditions NotBefore="2013-10-01T23:41:09.507Z" NotOnOrAfter="2013-10-02T00:41:09.507Z" > <AudienceRestriction> <Audience>https://jboss01.mytest.local:8443/hw/saml-hw</Audience> </AudienceRestriction> </Conditions> <AttributeStatement> <Attribute Name="http://mytest.local/SAM-Account-Name"> <AttributeValue>Jimmy.Li</AttributeValue> </Attribute> <Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/role"> <AttributeValue>SAMLUser</AttributeValue> </Attribute> </AttributeStatement> <AuthnStatement AuthnInstant="2013-10-01T23:41:09.455Z" SessionIndex="_610520ab-d49d-49cc-95fb-c82bcf555af8" > <AuthnContext> <AuthnContextClassRef>urn:federation:authentication:windows</AuthnContextClassRef> </AuthnContext> </AuthnStatement> </Assertion> </samlp:Response>
PicketLink Logging Level
* Replace log4j jar file in the server/default/lib directory with log4j-1.2.17.jar
* For JBoss 4.2.2, logging file is server/default/conf/jboss-log4j.xml
* Duplicate CONSOLE appender and name it CONSOLE2.
– Also set Threshold value to TRACE:
<appender name="CONSOLE2" class="org.apache.log4j.ConsoleAppender"> <errorHandler class="org.jboss.logging.util.OnlyOnceErrorHandler"/> <param name="Target" value="System.out"/> <param name="Threshold" value="TRACE"/> <layout class="org.apache.log4j.PatternLayout"> <!-- The default pattern: Date Priority [Category] Message\n --> <param name="ConversionPattern" value="%d{ABSOLUTE} %-5p [%c{1}] %m%n"/> </layout> </appender>
* Set logging level to TRACE for org.picketlink category and appender to CONSOLE2:
<category name="org.picketlink"> <priority value="TRACE" /> <appender-ref ref="CONSOLE2"/> </category>
Issues
keytool Import Error
* I copied ADFS signing certificate from ADFS metadata URL (https://hostname/federationmetadata/2007-06/federationmetadata.xml) and tried to do an import with
keytool -import -v -keystore samTrust.jks -alias adfs -sotrepass changeit -file adfs_sign.cer
* Error message:
keytool error: java.lang.Exception: Input not an x.509 certificate
* Solution: enclose the copied token signing certificate with
-----BEGIN CERTIFICATE----- token signing cert string goes here -----END CERTIFICATE-----
MSIS7004
* Error message in Event Viewer > Application and Services > AD FS 2.0 > Admin:
IdentityServer.Protocols.WSTrust.StsConnectionException: MSIS7004: An exception occurred while connecting to the federation service
* Solutions:
– I got this error because all my ADFS 2.0 certificates (IIS cert, signing cert, encryption cert) expired. You need to renew all certificates. See this post on how to renew ADFS 2.0 certificates.
– Also you need to enable net.tcp protocol for IIS sites. See this discussion and quoted here:
You need to add net.tcp to the enabled protocols of your site. Go to IIS Manager, right-click on your website, go to 'Manage Web Site' or 'Manage Application', then to 'Advanced Settings...'. There you see 'Enabled Protocols'. It probably says http. Change it to http,net.tcp
.
References
* PicketLink Download
* PicketLink 2.1.7 Doc
* UserGuide.pdf
* JBoss SecurityFAQ