Contents
Environment
* Windows Server 2008R2 Enterprise Edition
* Solaris 10 x64 u11
Prepare Windows Server
* See this post on how to install Windows Server 2008R2 on ESXi 5.1.
Install Identity Management for Unix
* Login Windows Server 2008R2.
* Open Start > Administrative Tools > Server Manager
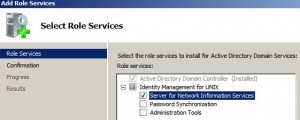
* Right click Server Manager > Roles > Active Directory Domain Service and select Add Role Services
* Select Server for Network Information Services
* Click Next and then Install.
* Restart server.
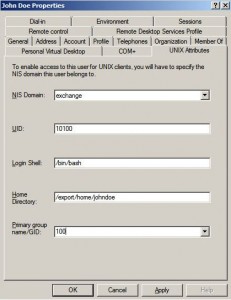
* Open Start > Administrative Tools > Active Directory Users and Computers. Check the presence of UNIX Attributes:
Tuning AD
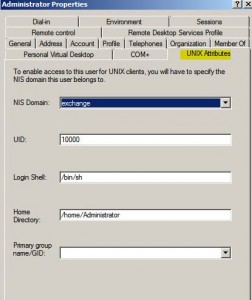
* These Solaris client attributes need to be tuned:
– uid
– uidnumber
– gid
– gidnumber
* Register Schema Management Snap-In
regsvr32 schmmgmt
* Open mmc console
mmc /a* Add Active Directory Schema snap-in:
File > Add/Remove snap-in… > Active Directory Schema
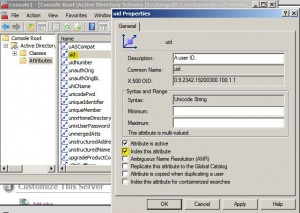
* Select Console Root > Active Directory Schema > Attributes
* Index attributes: uid, uidnumber, gid, gidnumber
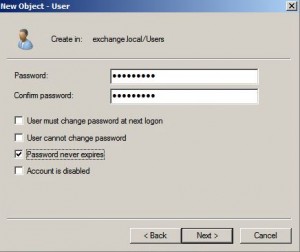
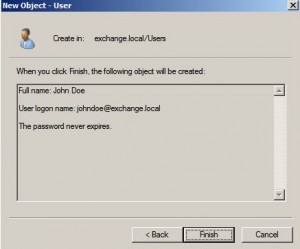
Provision a Unix User in AD
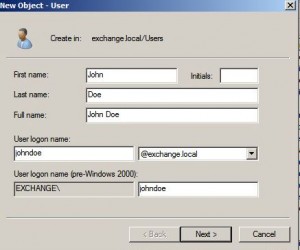
* Add a new user named johndoe to AD:
* With Unix attributes
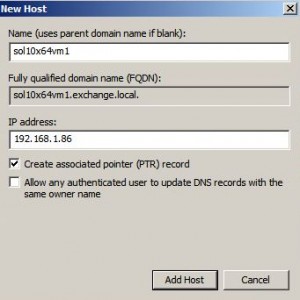
Configure DNS
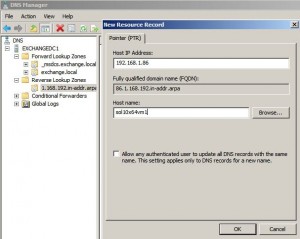
* Create a forward (A) and reverse (PTR) DNS record for Solaris client:
* Create a reverse (PTR) DNS record for AD server:
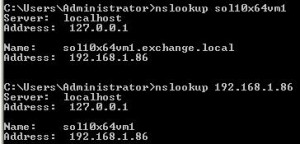
* Check that both forward and reverse lookup worked:
Synchronize Solaris Time to Windows Server NTP Service
Setup Windows 2008 R2 NTP Server
* Set HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Config\AnnounceFlags to 10
* Set HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpServer\Enabled to 1
* Restart w32time
net stop w32time && net start w32time
Setup Solaris NTP Client
cp /etc/inet/ntp.client /etc/inet/ntp.conf touch /var/ntp/ntp.drift vi /etc/inet/ntp.conf # With content: server Exchangedc1 driftfile /var/ntp/ntp.drift multicastclient 224.0.1.1
* Refresh daemon NTP
svcadm enable svc:/network/ntp svcadm refresh svc:/network/ntp svcadm restart svc:/network/ntp
* check status to make it’s status is online
svcs ntp STATE STIME FMRI online Jul_21 svc:/network/ntp:default
Configure Kerberos with adjoin Script
* Download adjoin-s10u5.tar.gz, for example, from here
* Copy adjoin-s10u5.tar.gz to sol10x64vm1 and unzip it:
gunzip -c adjoin-s10u5.tar.gz |tar xvf -
* Check resolv.conf and nsswitch.dns
* Run adjoin -f
* Verify setup with ldapsearch
ldapsearch -h Exchangedc1 -o mech=gssapi -o authzid='' -b "cn=sol10x64vm1,cn=computers,dc=exchange,dc=local" -s base "" cn version: 1 dn: cn=sol10x64vm1,cn=computers,dc=exchange,dc=local cn: SOL10X64VM1
* List Kerberos ticket cache:
klist Ticket cache: FILE:/tmp/krb5cc_0 Default principal: host/sol10x64vm1.exchange.local@EXCHANGE.LOCAL Valid starting Expires Service principal 07/22/13 19:52:26 07/23/13 05:52:26 krbtgt/EXCHANGE.LOCAL@EXCHANGE.LOCAL 07/22/13 19:52:26 07/23/13 05:52:26 ldap/exchangedc1.exchange.local@EXCHANGE.LOCAL
* List host keys
klist -e -k /etc/krb5/krb5.keytab Keytab name: FILE:/etc/krb5/krb5.keytab KVNO Principal ---- -------------------------------------------------------------------------- 2 host/sol10x64vm1.exchange.local@EXCHANGE.LOCAL (AES-256 CTS mode with 96-bit SHA-1 HMAC) 2 host/sol10x64vm1.exchange.local@EXCHANGE.LOCAL (AES-128 CTS mode with 96-bit SHA-1 HMAC) 2 host/sol10x64vm1.exchange.local@EXCHANGE.LOCAL (ArcFour with HMAC/md5) 2 host/sol10x64vm1.exchange.local@EXCHANGE.LOCAL (DES cbc mode with CRC-32) 2 host/sol10x64vm1.exchange.local@EXCHANGE.LOCAL (DES cbc mode with RSA-MD5)
* List /etc/krb5/krb5.conf file content:
cat /etc/krb5/krb5.conf [libdefaults] default_realm = EXCHANGE.LOCAL [realms] EXCHANGE.LOCAL = { kdc = exchangedc1.exchange.local kpasswd_server = exchangedc1.exchange.local kpasswd_protocol = SET_CHANGE admin_server = exchangedc1.exchange.local } [domain_realm] .exchange.local = EXCHANGE.LOCAL
* Verify presence of Unix attribute for user
ldapsearch -h Exchangedc1 -o mech=gssapi -o authzid='' -b "cn=users,dc=exchange,dc=local" "cn=John Doe" version: 1 dn: CN=John Doe,CN=Users,DC=exchange,DC=local objectClass: top objectClass: person objectClass: organizationalPerson objectClass: user cn: John Doe sn: Doe givenName: John distinguishedName: CN=John Doe,CN=Users,DC=exchange,DC=local ... uid: johndoe msSFU30Name: johndoe msSFU30NisDomain: exchange uidNumber: 10100 gidNumber: 100 unixHomeDirectory: /export/home/johndoe loginShell: /bin/bash
Initialize Solaris LDAP Client
* This allows Solaris host to access naming service from AD
Prerequisites
* DNS client is enabled:
svcadm enable svc:/nework/dns/client:default svcs -a |grep dns disabled Jul_20 svc:/network/dns/server:default online 18:34:27 svc:/network/dns/client:default
* nscs, which is Solaris caching daemon, is enabled in order to use per-user authentication functionality:
svcadm enable name-service-cache svcs -a |grep name-service online 19:53:01 svc:/system/name-service-cache:default
* /etc/resolv.conf file is properly configured:
cat /etc/resolv.conf domain exchange.local nameserver 192.168.1.30
* Both forward and reverse DNS lookup for AD server are successful
nslookup exchangedc1 nslookup 192.168.1.30
* /etc/nsswitch.ldap uses DNS for hosts and ipnodes
cat /etc/nsswitch.ldap|grep dns hosts: dns ldap [NOTFOUND=return] files ipnodes: dns ldap [NOTFOUND=return] files
Initialize with ldapclient
* Run ldapclient:
ldapclient -v manual \ -a credentialLevel=self \ -a authenticationMethod=sasl/gssapi \ -a defaultSearchBase=dc=exchange,dc=local \ -a domainName=exchange.local \ -a defaultServerList=192.168.1.30 \ -a attributeMap=passwd:gecos=cn \ -a attributeMap=passwd:homedirectory=unixHomeDirectory \ -a objectClassMap=group:posixGroup=group \ -a objectClassMap=passwd:posixAccount=user \ -a objectClassMap=shadow:shadowAccount=user \ -a serviceSearchDescriptor=passwd:cn=users,dc=exchange,dc=local?one \ -a serviceSearchDescriptor=group:cn=users,dc=exchange,dc=local?one
> > > > > > > > > > > > Parsing credentialLevel=self Parsing authenticationMethod=sasl/gssapi ... Arguments parsed: authenticationMethod: sasl/gssapi defaultSearchBase: dc=exchange,dc=local ... About to modify this machines configuration by writing the files Stopping network services Stopping sendmail ... ldap not running nisd not running nis(yp) not running file_backup: stat(/etc/nsswitch.conf)=0 file_backup: (/etc/nsswitch.conf -> /var/ldap/restore/nsswitch.conf) .. Starting network services start: /usr/bin/domainname exchange.local... success start: DNS client is enabled ... restart: sleep 100000 microseconds restart: milestone/name-services:default... success System successfully configured
* Restart LDAP client
svcadm restart svc:/network/ldap/client:default svcs -a|grep ldap online 19:54:08 svc:/network/ldap/client:default
* Verify the contents of LDAP client cache:
# ldapclient list NS_LDAP_FILE_VERSION= 2.0 NS_LDAP_SERVERS= 192.168.1.30 NS_LDAP_SEARCH_BASEDN= dc=exchange,dc=local NS_LDAP_AUTH= sasl/GSSAPI NS_LDAP_CACHETTL= 0 NS_LDAP_CREDENTIAL_LEVEL= self NS_LDAP_SERVICE_SEARCH_DESC= passwd:cn=users,dc=exchange,dc=local?one NS_LDAP_SERVICE_SEARCH_DESC= group:cn=users,dc=exchange,dc=local?one NS_LDAP_ATTRIBUTEMAP= passwd:homedirectory=unixHomeDirectory NS_LDAP_ATTRIBUTEMAP= passwd:gecos=cn NS_LDAP_OBJECTCLASSMAP= shadow:shadowAccount=user NS_LDAP_OBJECTCLASSMAP= passwd:posixAccount=user NS_LDAP_OBJECTCLASSMAP= group:posixGroup=group
Using Naming Service Switch and PAM
* cat /etc/nsswitch.conf
passwd: files ldap group: files ldap hosts: dns ldap [NOTFOUND=return] files ipnodes: dns ldap [NOTFOUND=return] files
* Add to /etc/pam.conf
login auth sufficient pam_krb5.so.1
other auth sufficient pam_krb5.so.1
other account required pam_krb5.so.1
other password sufficient pam_krb5.so.1
# grep pam_krb5 /etc/pam.conf login auth sufficient pam_krb5.so.1 krlogin auth required pam_krb5.so.1 krsh auth required pam_krb5.so.1 ktelnet auth required pam_krb5.so.1 other auth sufficient pam_krb5.so.1 other account required pam_krb5.so.1 other password sufficient pam_krb5.so.1
* getent
# getent passwd johndoe johndoe:x:10100:100:John Doe:/export/home/johndoe:/bin/bash
* ldaplist
# ldaplist -l passwd johndoe dn: gecos=John Doe,gecos=Users,DC=exchange,DC=local objectClass: top objectClass: person objectClass: organizationalPerson objectClass: posixAccount cn: John Doe sn: Doe givenName: John distinguishedName: CN=John Doe,CN=Users,DC=exchange,DC=local ... uid: johndoe msSFU30Name: johndoe msSFU30NisDomain: exchange uidNumber: 10100 gidNumber: 100 homedirectory: /export/home/johndoe loginShell: /bin/bash gecos: John Doe
* Create home directory for johndoe
mkdir /export/home/johndoe chown johndoe /export/home/johndoe
* Login as johndoe
bash-3.2$ id uid=10100(johndoe) gid=100 bash-3.2$ klist Ticket cache: FILE:/tmp/krb5cc_10100 Default principal: johndoe@EXCHANGE.LOCAL Valid starting Expires Service principal 07/22/13 21:07:06 07/23/13 07:07:06 krbtgt/EXCHANGE.LOCAL@EXCHANGE.LOCAL renew until 07/29/13 21:07:06 07/22/13 21:07:06 07/23/13 07:07:06 ldap/exchangedc1.exchange.local@EXCHANGE.LOCAL renew until 07/29/13 21:07:06
Test Password Management
* Login as johndoe and change password with kpasswd (not passwd)
Useful Tools
Export ldif File from AD: ldifde
ldifde -f johndoe.ldif -d "CN=John Doe,CN=USERS,DC=exchange,DC=local"
ldapadd
* ldapadd command example:
ldapadd -h exchangedc1 -D "cn=Administrator,cn=users,dc=exchange,dc=local" -w "Welcome1" -f johndoe2.ldif -v
* johndoe2.ldif
dn: cn=John Doe2,cn=Users,dc=exchange,dc=local objectClass: user cn: John Doe2 sn: Doe2 givenName: John distinguishedName: cn=John Doe2,cn=Users,dc=exchange,dc=local displayName: John Doe2 sAMAccountName: johndoe2 userPrincipalName: johndoe2@exchange.local accountExpires: 0 msSFU30NisDomain: exchange uid: johndoe2 uidNumber: 10102 gidNumber: 100 unixHomeDirectory: /export/home/johndoe2 loginShell: /bin/bash
ldapmodify
ldapadd -h exchangedc1 -D "cn=Administrator,cn=users,dc=exchange,dc=local" -w "Welcome1" -f johndoe2b.ldif -v
* johndoe2.ldif
dn: cn=John Doe2,cn=Users,dc=exchange,dc=local changetype: modify replace: userAccountControl userAccountControl: 512
* Note that this example does not work.
References
* kerberos_s10.pdf
* Solaris 10 and Active Directory Integration
* Solaris Authentication Login with Active Directory
* Joining Unix-like systems to an Active Directory
* Solaris : automatic creation of home dirs
* Authenticating UNIX/Linux to Windows 2008R2. Part 2 : Solaris 10
* Creating Active Directory Accounts



They are stratum 2 sevrers: they peer with eachother, two other internal NTP sevrers, and three upstream clocks, but the three upstreams are identical. There is no local clock source (GPS, etc.). One of them is an Atom 330 and the other a Dell PowerEdge 850. All of the internal peers are real hardware since the clock drift on VMs is unacceptable. All of our sevrers run Debian.The iburst option is fine, just not burst . These sevrers were already available to our colocation and dedicated server customers internally on a different IP address, we just opened an additional IPv6 address to public access. At some point in the future we may add a local PPS source via GPS or similar.
With Windows 2016+ Server for Network Information Services do not exist anymore. How to integrate NIS with AD. Is there is a Solaris version of SSSD?