Overview
What is SAML
* SAML stands for Security Assertion Markup Language
* Is an XML based standard maintained by OASIS
* SAML 1.0 approved in 2002
* SAML 2.0 approved in 2005
SAML 2 New Features
* Authentication request protocol: flow starts at the SP who issues an explicit authentication request to IdP.
What SAML Provides
* Provides single sign-on (SSO) solution in a cross domain environment
* Defines a framework for exchanging authentication/authorization information across domains in the form of assertions instead of tokens
* Defines a language for
– expressing assertions
– protocols for requesting and obtaining assertions from SAML authorities
– bindings for mapping SAML onto messaging and transport protocols
Asserting Party
* aka SAML authorities
* The system, or administrative domain, that asserts information about a subject.
* Example:
This user is JohnDoe, he has an email address of john.doe@acompany.com, and he was authenticated into this system using a password mechanism.
Relying Party
* The system, or administrative domain, that relies on information supplied to it by the asserting party.
Addressed Issues
* Limitations of browser cookies
* SSO interop
* Web services
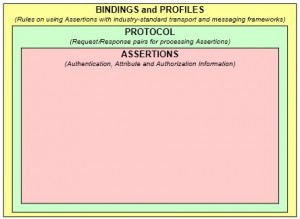
SAML Architecture
Assertions
* Assertion is a claim, statement, or declaration of a fact made by a SAML authority
* There are three types of assertions:
– Authentication assertion: the subject is authenticated
<saml:AuthnStatement AuthnInstant="2005-04-01T16:57:30.000Z"> <saml:AuthnContext> <saml:AuthnContextClassRef> urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport </saml:AuthnContextClassRef> </saml:AuthnContext> </saml:AuthnStatement>
– Authorization assertion: the subject is authorized to access a particular resource
<saml:AuthzDecisionStatement> Resource="http://CarRentalInc.com/doit.cgi" Decision="Permit"> <saml:Action>Execute</saml:Action> </saml:AuthzDecisionStatement>
– Attribute assertion: the subject is associated with the supplied attribute
<saml:AttributeStatement> <saml:Attribute Name="PaidStatus"> <saml:AttributeValue>Paid</saml:AttributeValue> </saml:Attribute> </saml:AttributeStatement>
Protocol
* SAML defines a request/response protocol for obtaining assertions.
Bindings
* Details exactly how the SAML protocol maps onto transport and messaging protocols.
* Examples: SOAP over HTTP binding.
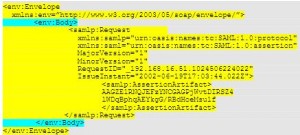
* Request example:
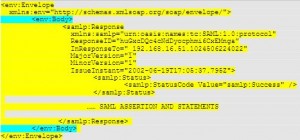
* Response example2:
Profiles
* Technical descriptions of particular flows of assertions and protocol messages that define how SAML can be used for a particular purpose.
* Derived from use cases.
* SAML 1.1 defines two profiles:
– Browser/Artifact Profile: A reference is sent to relying party which is used by relying party to pull assertion from Assertion Party.
– Browser/POST Profile: An assertion is POSTed directory to relying party.
Browser/Artifact Profile: Source-Site-First Processing
Traditional Single Sign-On Solutions
* Trusted tickets
* Synchronized credentials
* Pseudonym services
SAML Components
* Credential collector: collects user credentials
* Session authority: maintains session state
* Authentication authority: produces authentication assertions
* Attribute authority: produces attribute assertions
* Attribute repository: to store attribute assertions
Common Elements
* Issuer
* ds:Signature: issuer signed signature
* Subject: to which assertions apply
* Conditions: must be evaluated before using assertions
* Advice: additional info to assist processing of assertions
Assertion Statements
Assertion contains 0..* of
* AuthnStatement: authentication statement
* AuthzDecisionStatement: authorization statement
* AttributeStatement: attribute statement
* Statement: custom statement
EncryptedAssertion Element
* xenc:EncryptedData
* xenc:EncryptedKey
Example
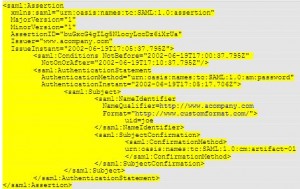
<saml:Assertion Version="2.0" ID="_34234se72" IssueInstant="2005-04-01T16:58:33.173Z"> <saml:Issuer>http://authority.example.com/</saml:Issuer> <ds:Signature>...</ds:Signature> <saml:Subject> <saml:NameID format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"> jygH5F90l </saml:NameID> </saml:Subject> <saml:AuthnStatement AuthnInstant="2005-04-01T16:57:30.000Z"> <saml:AuthnContext> <saml:AuthnContextClassRef> urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport </saml:AuthnContextClassRef> </saml:AuthnContext> </saml:AuthnStatement> </saml:Assertion>
Example
<?xml version="1.0" ?> <S11:Envelope xmlns:S11="http://schemas.xmlsoap.org/soap/envelope/" xmlns:S12="http://www.w3.org/2003/05/soap-envelope"> <S11:Header xmlns="http://docs.oasis-open.org/wss/2004/01/ oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/ oasis-200401-wss-wssecurity-secext-1.0.xsd"> <Security S11:actor="..." S11:mustUnderstand="..." S12:role="..."> <saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" MajorVersion="1" MinorVersion="1" AssertionID="_abf73415-02c3-1149-79c2-974523690365" Issuer="www.xyz.com" IssueInstance="2004-12-28T09:14:33Z"> <saml:Conditions NotBefore="2004-12-28T09:15:00Z" NotAfter="2004-12-28T09:30:00Z" /> <saml:AuthenticationStatement AuthenticationMethod="urn:oasis:names:tc:SAML:1.0:am:password" AuthenticationInstance="2004-12-28T09:14:24Z"> <saml:Subject> <saml:NameIdentifier SecurityDomain="www.xyz.com" Name="sample1" /> </saml:Subject> </saml:AuthenticationStatement> ... </saml:Assertion> </Security> ... </S11:Header> <S11:Body> ... </S11:Body> </S11:Envelope>
SAML Implementations
* ADFS
* WebLogic
* SAML Open Source Implementations
– Shibboleth
References
* SAML Wiki
* Security Assertion Markup Language(SAML) V2.0 Technical Overview
* SAML Spec
* SAML 2: The Building Blocks of Federated Identity
* http://www.cs.ucsb.edu/~bultan/courses/595-W06/SAML.pdf