Contents
Steps
* Login domain controller as Administrator
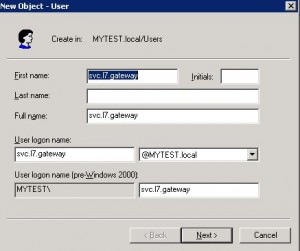
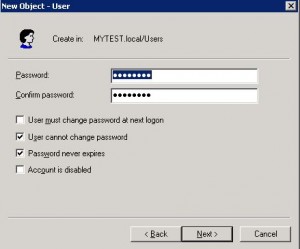
* Create a service account in AD, e.g. svc.l7.gateway:
* Issue ktpass command:
ktpass -princ HTTP/layer7.mytest.local@MYTEST.LOCAL -mapuser svc.l7.gateway -pass Welcome1 -out c:\layer7.keytab
* Output:
C:\Documents and Settings\Administrator>ktpass -princ HTTP/layer7.mytest.local@M YTEST.LOCAL -mapuser svc.l7.gateway -pass Welcome1 -out c:\layer7.keytab Targeting domain controller: DC01.MYTEST.local Successfully mapped HTTP/layer7.mytest.local to svc.l7.gateway. WARNING: pType and account type do not match. This might cause problems. Key created. Output keytab to c:\layer7.keytab: Keytab version: 0x502 keysize 72 HTTP/layer7.mytest.local@MYTEST.LOCAL ptype 0 (KRB5_NT_UNKNOWN) vno 2 etype 0x17 (RC4-HMAC) keylength 16 (0xcf3a5525ee9414229e66279623ed5c58)
References
* Generating the Keytab File and Mapping the Service Principal Name
* Ktpass