Contents
This is part of 1Z0-451: Oracle SOA Foundation Practitioner Exam
<< Previous
Explain Web Services and Composite Security
Overview
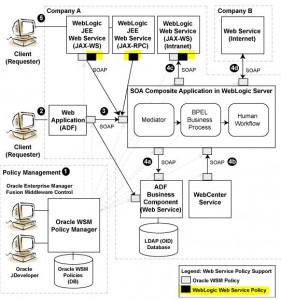
* Two categories of Oracel WS:
– Oracle Infra WS
– WebLogic (JEE) WS
* Two types of policies (only a subset can interop):
– WSM Policies
– WL WS Policies
WSM Policies
* Provided by WSM
* Can be attached using JDev to
– SOA
– ADF
– WebCenter WS
* Can also be attached to JAX-WS WS but not to JAX-RPC WS
* Managed from EM or WLST
WebLogic WS Policies
* Provides by WLS
* Only a subset can interop with WSM policies
* Managed from WL Console
Security Types
* Authentiation
* Authorization (or Access Control)
* Confidentiality
* Integrity (or non-repudiation)
Security Levels
Transport Level Security
* Provided by SSL
* Only protects data in transit
Application (or Message) Level Security
* Provided by WS-Security (XML Encryption, XML Security)
* Support five types of security tokens:
– Username
– X.509
– Kerberos
– SAML
– REL (rights markup)
Describe the Fusion Middleware security architecture
* See Securing SOA Composite Applications
Understand Security Policy Management, Identity Propagation
Describe OWSM Agents
WSM Overview
* Provides a policy framework to manage and secure web services consistently across organization
* Can be at design time (by developers) and run time (by admins)
* Based WS-Policy standard
PEP => OPSS => WLS Sec
WSM Tasks
* Handle WS-Security
* Define auth/authn policies against an LDAP directory
* Generate standard security tokens (e.g. SAML tokens) to propagate identities across multiple web services used in a single transaction
* Segment policies into different namespaces by creating policies within different folders
* Examine log files
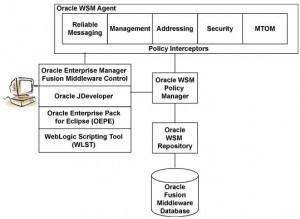
Main Components of WSM Architecture
* EM: enable admins to manage, secure, monitor web services
* JDev
* WSLT: command line tools
* Policy Manager: reads/writes policies (either predefined or custom policies) from Oracle WSM Repository
* WSM Agent: Manages the enforcement of policies via the Policy Interceptor Pipeline
* Policy Interceptors: enforces policies which include:
– reliable messaging
– management
– addressing
– security
– MTOM
* WSM Repository (db or file system): stores WSM metadata such as:
– policies: comprise of one or more policy assertions of the same policy category (WS-RM, Management, Addressing, Security, MTOM)
– policy sets
– assertion templates
– policy usage data
* MDS: as WSM repository
References
* Understanding Oracle WSM Policy Framework
* Oracle® Fusion Middleware Security and Administrator’s Guide for Web Services 11g Release 1 (11.1.1)
Next >> SOA 11g Integration Points