Contents
* This is the note I took following the steps to setup SAML1.1 SSO solution as described in the references.
* I used two Oracle virtual boxes downloaded from here.
* I named one virtual box wlbox1 and function as IdP (i.e. SAML Provider) and the other wlbox as SP (i.e.SAML consumer).
Setup a New Security Realm
* This needs to be done on both SAML 1.1 source and destination sites.
Add and Configure a New Security Realm
* Add a new realm: saml11realm
* Add a new Authentication Provider: saml11DefAuthP; set type to DefaultAuthenticator.
* Add a new Authentication Provider: saml11DefIdAsserter; set type to DefualtIdentityAsserter; Set its Active Types to AuthenticatedUser
* Add a new Password Validation: saml11SysPassVal; set type to SystemPasswordValidator
* Add a new XACML Authorization Provider: saml11XACMLAuthorizer; set type to XACMLAuthorizer
* Add a new Adjudicator: saml11DefAdj; set type to DefaultAdjudicator
* Add a new XACML Role Mapper: saml11XACMLRoleMapper; set type to XACMLRoleMapper
* Add a new Auditing Provider: saml11DefAuditP; set type to DefualtAuditor
* Add a new SAMLCredentialMapperV2: saml11CredMapperv2; set type to XAMLCredentialMapperV2
* Add a new Certification Path: select type WebLogicCertPathProvider; name: saml11WLCertPath; check Current Builder
Change Default Realm
* Set default realm to saml11realm: domain > Security > General > Default realm
* Backup config.xml and restart WebLogic
Setup SSL
* See this post
Add New User
* Add a new user: ssouser/welcome1
Configure Source Site
* The source site uses SAML Credential Mapper V2 to produce SAML assertions
Setup SAMLCredentialMapperV2
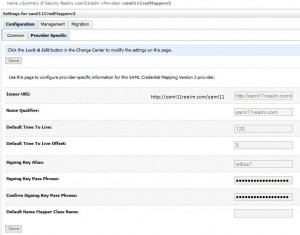
* Go to domain > Security Realms > saml11realm > Providers > Credential Mapping > saml11CredMapperv2 > Configuration > Provider Specific
* Click Lock & Edit and enter:
– Issuer URI: http://saml11realm.com/saml11
– Name Qualifier: saml11realm.com
– Default Time To Live: 120
– Default Time To Live Offset: 5
– Signing Key Alias: wlbox1
– Signing Key Pass Phrase: secret
* Click Save and Activate Change
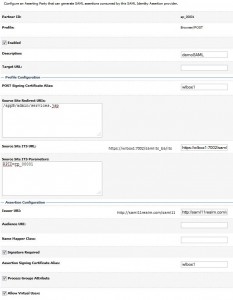
Setup Relying Parties
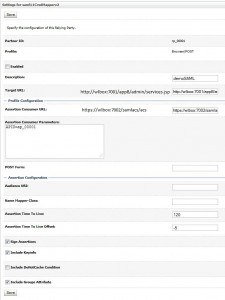
* Go to Security Realms > saml11realm > Providers > Credential Mapping > saml11CredMapperv2 >Management > Relying Parties > New
– Profile: Browser/POST
– Description: demoSAML
* Click newly created relying party, i.e. rp_00001, and enter:
– Enabled: true
– Target URL: http://wlbox:7001/appB/admin/services.jsp
– Assertion Consumer URL: https://wlbox:7002/samlacs/acs
– Assertion Consumer Parameters: APID=ap_00001
– Assertion Time To Live: 120
– Assertion Time To Live Offset: -5
– Sign Assertions: checked
– Include Keyinfo: checked
* Click Save
Configure SAML 1.1 Source Side Federation Services
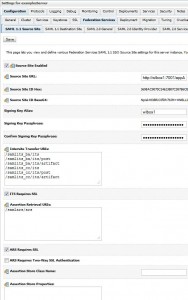
* Go to domain > Environment > Servers > examplesServer > Configuration > Federation Services > SAML 1.1 Source Site
* Click Lock & Edit and enter:
– Source Site Enabled: true
– Source Site URL: http://wlbox1:7001/appA
– Signing Key Alias: wlbox1
– Signing Key Passphrase: secret
– Intersite Transfer URIs:
/samlits_ba/its /samlits_ba/its/post /samlits_ba/its/artifact /samlits_cc/its /samlits_cc/its/post /samlits_cc/its/artifact
* ITS Requires SSL: checked
* Assertion Retrieval URIs:
/samlars/ars
* ARS Requires SSL: checked
* Click Save and Activate Changes
Configure Destination Site
* Uses SAML Identity Assertion Provider V2 to consume SAML 1.1 identity assertions to allow SAML SSO.
Import Source Site Certificate
* Copy source site (wlbox1) signing certificate to destination site (wlbox)
cd ~/identity [oracle@wlbox identity]$ ls cacert.pem wlbox1.pem wlbox.keystore wlbox.truststore
* Add a new SAMLIdentityAsserterV2: saml11SAMLIdA
* Restart WebLogic
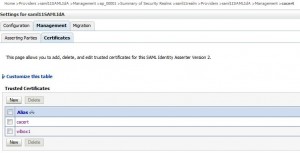
* Go to domain > Security Realms > saml11realm > Providers > Authentication > saml11SAMLIdA > Management > Certificate
* Click New and enter
– Alias: cacert
– Path: /home/oracle/identity/cacert.pem
* Click New and enter
– Alias: wlbox1
– Path: /home/oracle/identity/wlbox1.pem
* Click OK
Configure Asserting Party Properties
* This registers parties whose SAML assertions will be accepted
* Go to domain > Security Realms > saml11realm > Providers > Authentication > saml11SAMLIdA > Management > Asserting Parties
* Click New and enter:
– Profile: Browser/POST
– Description: demoSAML
* Click Save
* Click the newly created asserting party, e.g. ap_00001, and enter:
– Enabled: true
– Target URL: http://wlbox1:7001/appA #Not needed. This is for web services configurations
– POST Signing Certificate Alias: wlbox1
– Source Site Redirect URIs: /appB/admin/services.jsp
– Source Site ITS URL: https://wlbox1:7002/samlits_ba/its
– Source Site ITS Parameters: RPID=rp_00001
– Issuer URI: http://saml11realm.com/saml11
– Signature Required: true
– Asserting Signing Certificate Alias: wlbox1
* Click Save
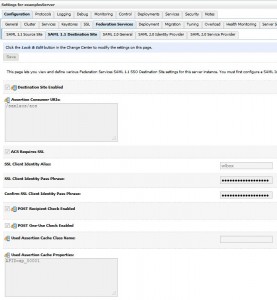
Configure SAML 1.1 Destination Side Federation Services
* Go to domain > Environment > Servers > examplesServer > Configuration > Federation Services > SAML 1.1 Destination Site
* Click Lock & Edit and enter:
– Destination Site Enabled: true
– Assertion Consumer URIs: /samlacs/acs
– ACS Requires SSL: true
– SSL Client Identity Alias: wlbox #Note: this is the destination machine server key
– SSL Client Identity Pass Phrase: secret
– POST Recipient Check Enabled: true
– POST one Use Check Enabled: true
– Used Assertion Cache Properties: APID=ap_00001
* Click Save and Activate Changes
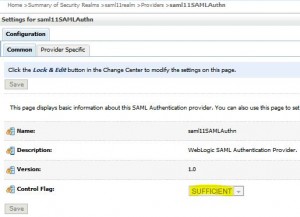
Add a New SAML Identity Assertion Provider
* Go to domain > Security Realms > saml11realm > Providers > Authentication
* Click Lock & Edit
* Click New and enter:
– Name: saml11SAMLAuthn
– Type: SAMLAuthenticator
* Click Save
* Click the newly created saml11SAMLAuthn and go to Configuration > Common
* Set
– Control Flag: SUFFICIENT
* Click Activate Changes
* Restart WebLogic
Enable Virtual Users
* A virtual user is a user who is authenticated on the SAML Identity Provider and this user is transferred ( with all his attributes and roles ) in a SAML Token to the Service Provider.
* This user does not need to exists on the WebLogic server of the Service Provider.
Enable Allow Virtual Users
* Go to domain > Security Realms > saml11realm > Providers > Authentication > saml11SAMLIdA > Management > Asserting Parties > ap_00001
* Click Lock & Edit
* Check Allow Virtual Users
* Click Save and Activate Changes
Enable Group Attributes
* By default, WebLogic SAML1.1 does not include group attributes in the generated SAML token.
* To enable it:
* On source site, go to Home >Summary of Security Realms >saml11realm >Providers >Authentication > saml11CredMapperv2 >Management >rp_00001
– Check Include Groups Attribute at the bottom of the page
* On target site, go to Home >Summary of Security Realms >saml11realm >Providers >saml11SAMLAuthn >Management >ap_00001
– Check Process Groups Attribute at the bottom of the page
Test
* Download sso-with-saml-134555.zipand unzip into a temp directory. You’ll see appA.war and appB.war files.
* Start JDeveloper and create a new application named, e.g. test.saml11
* Import both appA and appB into the JDev application.
* Modify URLs containing localhost to appropriate host names in following files:
– appA/Web Content/admin/auth.jsp
* Deploy appA to wlbox1
* Deploy appB to wlbox
Turn on Debugging
* Go to domain > Environment > Servers > examplesServer > Debug
* Click Lock & Edit
* Go to and check: weblogic > security > saml
* Click Enable and Activate Changes
Test SSO
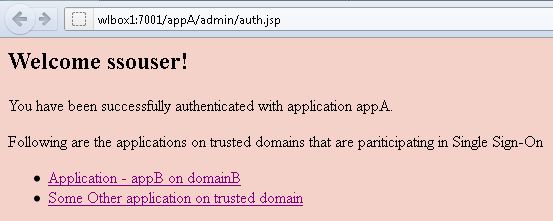
Access appA First
* Go to http://wlbox1:7001/appA/login.jsp
* Enter
– Username: ssouser
– Password: welcome1
* Once logged in, click Application – appB on domainB link
* appB on destination site is shown
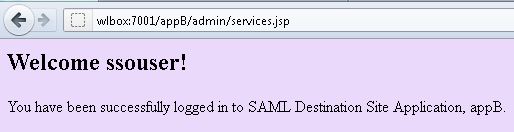
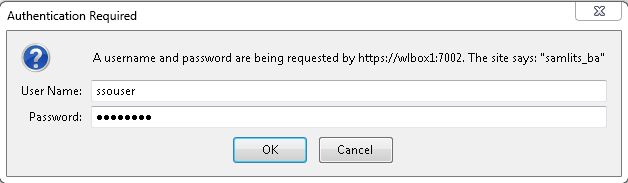
Access appB First
* Go to http://wlbox:7001/appB/admin/services.jsp
* Enter username and password when prompted
* appB/admin/services.jsp page is shown
Issues
LoginException while asserting identity, returning SC_FORBIDDEN
* Error message:
####<Jan 24, 2012 11:05:59 PM PST> <Debug> <SecuritySAMLAtn> <wlbox> <examplesServer> <[ACTIVE] ExecuteThread: '3' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <e6ea830ad360905e:-7b11c7e8:13513abed61:-8000-0000000000000026> <1327475159603> <BEA-000000> <SAMLAssertion: Assertion contains NotBefore condition> ####<Jan 24, 2012 11:05:59 PM PST> <Debug> <SecuritySAMLAtn> <wlbox> <examplesServer> <[ACTIVE] ExecuteThread: '3' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <e6ea830ad360905e:-7b11c7e8:13513abed61:-8000-0000000000000026> <1327475159603> <BEA-000000> <SAMLAssertion: Assertion contains NotOnOrAfter condition> ####<Jan 24, 2012 11:05:59 PM PST> <Debug> <SecuritySAMLAtn> <wlbox> <examplesServer> <[ACTIVE] ExecuteThread: '3' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <e6ea830ad360905e:-7b11c7e8:13513abed61:-8000-0000000000000026> <1327475159603> <BEA-000000> <SAMLAssertion: [Security:099031]Assertion is invalid before Tue Jan 24 23:06:04 PST 2012.> ####<Jan 24, 2012 11:05:59 PM PST> <Debug> <SecuritySAMLService> <wlbox> <examplesServer> <[ACTIVE] ExecuteThread: '3' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <e6ea830ad360905e:-7b11c7e8:13513abed61:-8000-0000000000000026> <1327475159603> <BEA-000000> <SAMLDestinationSiteHelper: doLogin: LoginException while asserting identity, returning SC_FORBIDDEN: javax.security.auth.login.LoginException: [Security:090377]Identity Assertion Failed, weblogic.security.spi.IdentityAssertionException: [Security:090377]Identity Assertion Failed, weblogic.security.spi.IdentityAssertionException: [Security:099031]Assertion is invalid before Tue Jan 24 23:06:04 PST 2012.> ####<Jan 24, 2012 11:05:59 PM PST> <Debug> <SecuritySAMLService> <wlbox> <examplesServer> <[ACTIVE] ExecuteThread: '3' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <e6ea830ad360905e:-7b11c7e8:13513abed61:-8000-0000000000000026> <1327475159603> <BEA-000000> <SAMLSingleSignOnService.doACSGet: Login failed, returning>
* Cause: there are time differences between source site and destination site
* Fix: Adjust TTL for both credential mapper and relying party, e.g:
– Assertion Time To Live: 120
– Assertion Time To Live Offset: -5
Error 403–Forbidden
* Error message:
####
####
####
* Cause: source site certificate not setup correctly.
* Fix: see Import Source Site Certificate.
– Check expiration date for the trusted certificates. Re-import if necessary.
References
* Configuring Single Sign-On with Web Browsers and HTTP Clients
* Configuring Single Sign-On using SAML in WebLogic Server 9.2
* SSO with WebLogic 10.3 and SAML
* http://htotapally.blogspot.com/2010/08/single-sign-on-using-weblogic-103-and.html

Pingback: WebLogic11g: Single Sign On with… « oracle fusion identity